← All Tutorials
Secure Remote Control with 2FA, End-to-End Encryption and TLS 1.3
In the current context, marked by an increasing need for work flexibility and a constant evolution of cyber threats, security in remote computer access assumes critical importance. The continuous rise in cyber attacks paints a picture of threats that are rapidly and constantly evolving. Companies requiring remote technical support services, especially for their server infrastructure, want assurance that the software tools used guarantee the highest level of security.
Iperius Remote is one of the best free software for remote control of PCs, MACs, Servers, and mobile devices. It is an excellent alternative to AnyDesk and TeamViewer, with all the necessary security requirements to comply with recent HIPAA and GDPR regulations. Iperius Remote positions itself as a cutting-edge solution, offering a set of advanced features that elevate standards of security, privacy, and control for users and companies. This article describes how Iperius Remote meets the challenges of security in remote access, combining technological innovation and ease of use.
Multi-factor Authentication (2FA) and Settings Protection
The safest way to protect a remote computer is to use two-factor authentication (2FA). In simple terms, this means that anyone wishing to connect to that computer must generate an OTP from an authorized mobile device, thus preventing any access that has not passed this additional level of authentication, even if a malicious user somehow obtains the remote computer’s ID and password. Setting up two-factor authentication is easy with Iperius Remote. Once the program is opened on the remote machine to be protected, go to the security options and enable the 2FA option. A QR code will be displayed, which can be scanned with a compatible authentication app like Google Authenticator, via our mobile device. Once done, close the window with the QR code. From that moment on, every time someone attempts to connect to that remote computer, the randomly generated OTP from the authentication app will be required.
All the steps to configure 2FA in Iperius Remote can be found in this tutorial.
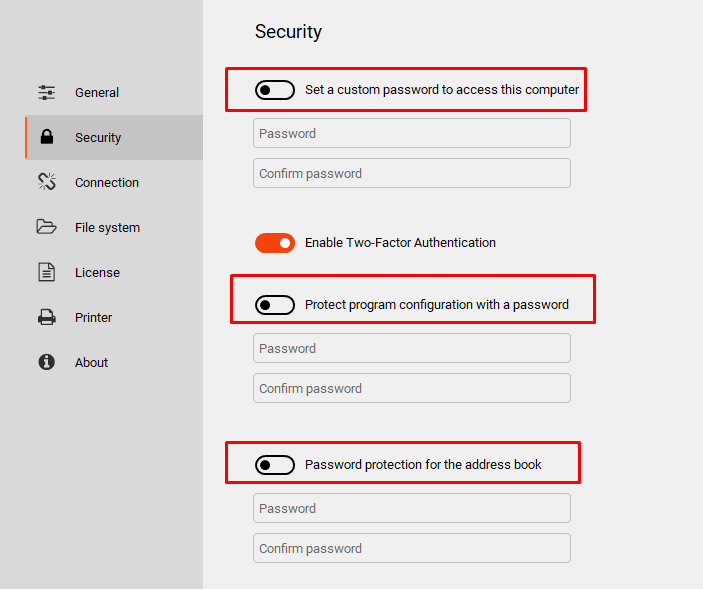
Iperius Remote goes further, allowing the setting of dedicated passwords to access the remote computer, protect the software settings, and secure access to the address book:
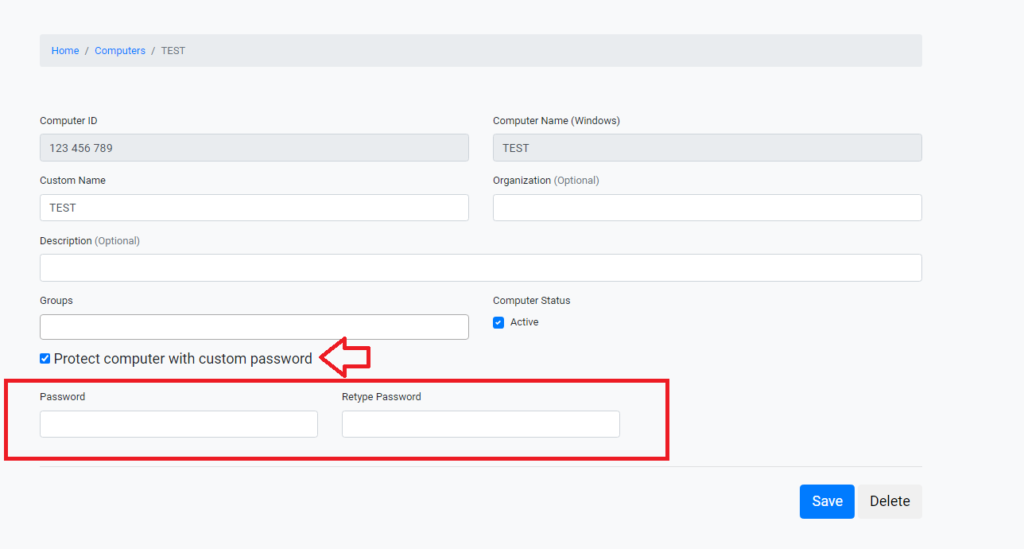
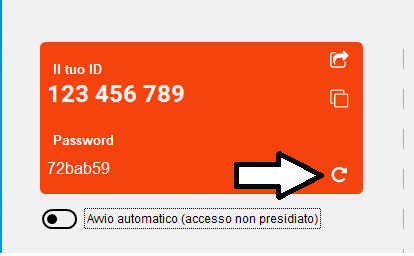
Moreover, Iperius Remote enables granular permission settings through its web administrative interface, where it is possible to configure access and viewing permissions in the address book for different computers, granularly for operator users and computer groups. It is also possible to set an additional password to access a specific computer (image below):
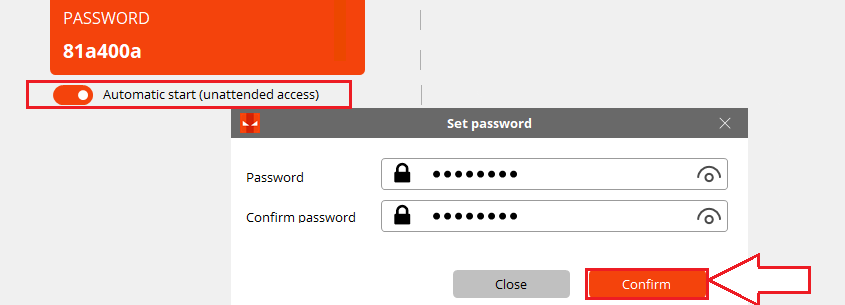
Custom Security and Advanced Control
Iperius Remote introduces the possibility of setting up unattended access with custom passwords, allowing users to access their computers remotely without the need for direct interaction but with the peace of mind of a secure and personal password..
In cases where unattended access cannot be enabled but the highest level of security is still desired, Iperius has added the functionality of password regeneration. With a simple click, security is further strengthened by allowing easy and quick change of access credentials to prevent misuse.
Innovations for Privacy and Data Security
Iperius Remote allows to choose what to share during the remote session.
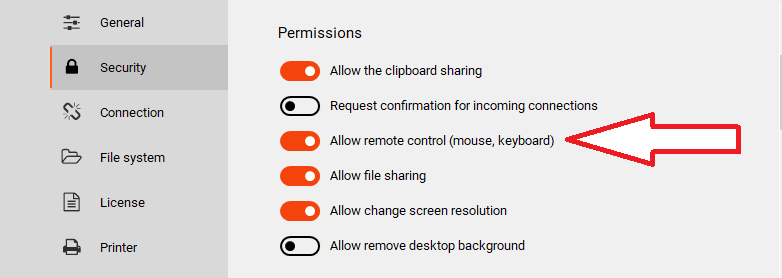
For example, a significant new feature is the ability to disable remote control, which allows you to show the screen without relinquishing control of the PC, ideal for support, demonstrations, or remote training.
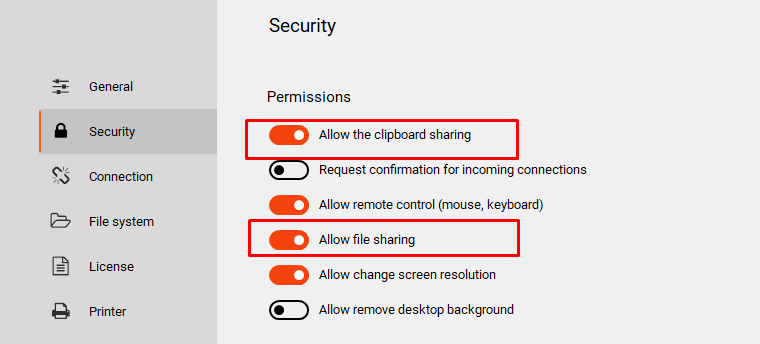
It is also possible to decide whether to allow clipboard and file sharing, a great way to prevent unwanted file or text transfer:
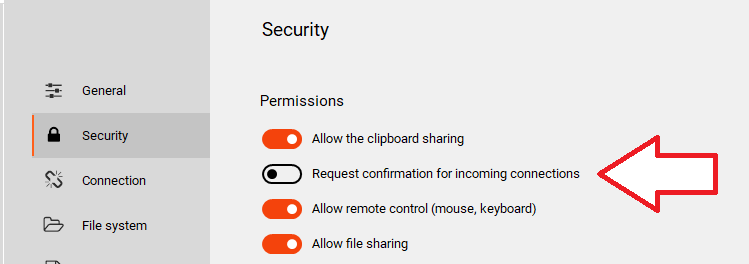
But one of the most important security features is definitely the “Request confirmation for incoming connections” option, which allows, for each incoming connection, to accept the connection and choose what to allow during the remote session.
For example, it is possible to accept the remote connection, allow remote control, but not allow clipboard and file sharing:
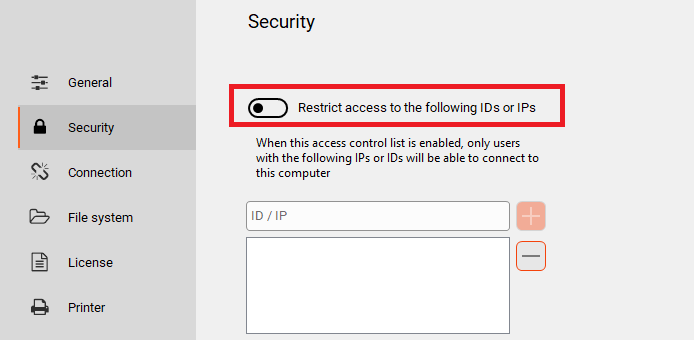
A very useful setting in Iperius Remote is the filter on incoming IDs/IPs, in such a way as to allow access only to IDs or IPs listed:
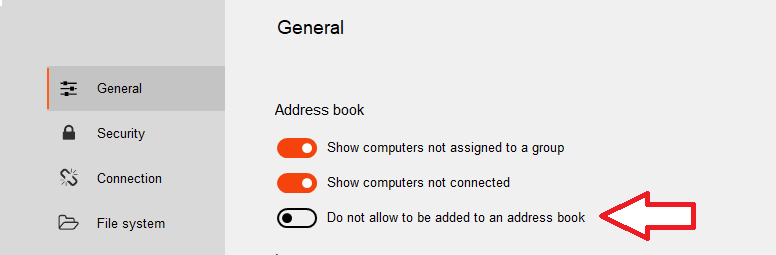
Iperius Remote also introduces the possibility to disable the addition of one’s device in external address books, offering users unprecedented control over their privacy and the dissemination of their information.
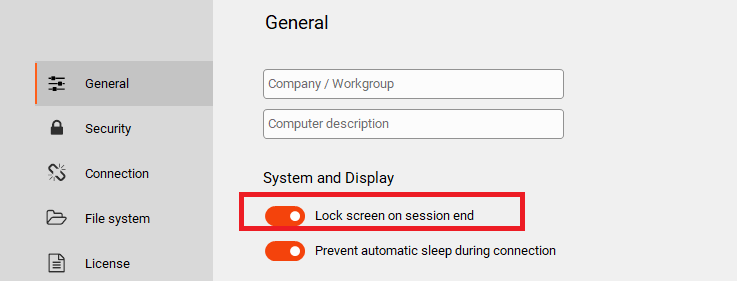
Finally, it is possible with Iperius to enable automatic screen locking at the end of a remote desktop session:
End-to-End Encryption with Advanced Protocols
Perhaps the most relevant aspect of Iperius Remote’s security is the use of end-to-end encryption for connections between clients and the use of cutting-edge protocols such as TLS 1.3.
End-to-end encryption (E2EE) represents a specific security technique in which data is encrypted at every stage of its transfer from one device to another. This technique ensures that communication is protected by preventing third parties from accessing the content of the transmitted data, both during the transfer between devices and when data passes through a server. Iperius Remote natively implements end-to-end encryption in all video transmissions (remote desktop), file transfers, and chat, thus avoiding any possibility of interception or compromise of data. This technology ensures that all transmitted data are encrypted from one end of the communication channel to the other, protecting the information from interceptions and manipulations.
All connections of Iperius Remote are protected via AES encryption or password hashing and rely on a server infrastructure in ISO 27001 certified data centers with proactive protection from DDOS attacks, ensuring the highest reliability of the service.
Conclusion
Iperius Remote confirms itself as a leading solution for those looking for secure, reliable and feature-rich remote access. From multi-factor authentication to end-to-end encryption, customizable security options and advanced controls, every aspect was designed with maximum security and ease of use in mind.
Iperius Remote is the right choice for businesses, IT professionals and security-conscious users who want to navigate the world of remote access with confidence.
For any questions or doubts regarding this tutorial,
Contact us